The era that was “move fast and break things” in cloud will be finally over. cloud environment for enterprises has evolved from simple migration to complicated orchestration. Organisations are no longer only controlling virtual machines or storage buckets theyre overseeing multiple multi cloud environments across different platforms servers serverless infrastructures and most importantly they are rapidly growing AI as well as Machine Learning workloads.
The meaning of Cloud Governance is evolving. Its no longer merely function of gatekeeper that can tell “no.” By 2026 Cloud Governance Framework is an engine for enabling. Its set of policies rules and processes automated to allow an organisation to be able to use speed of cloud without wrecking car.
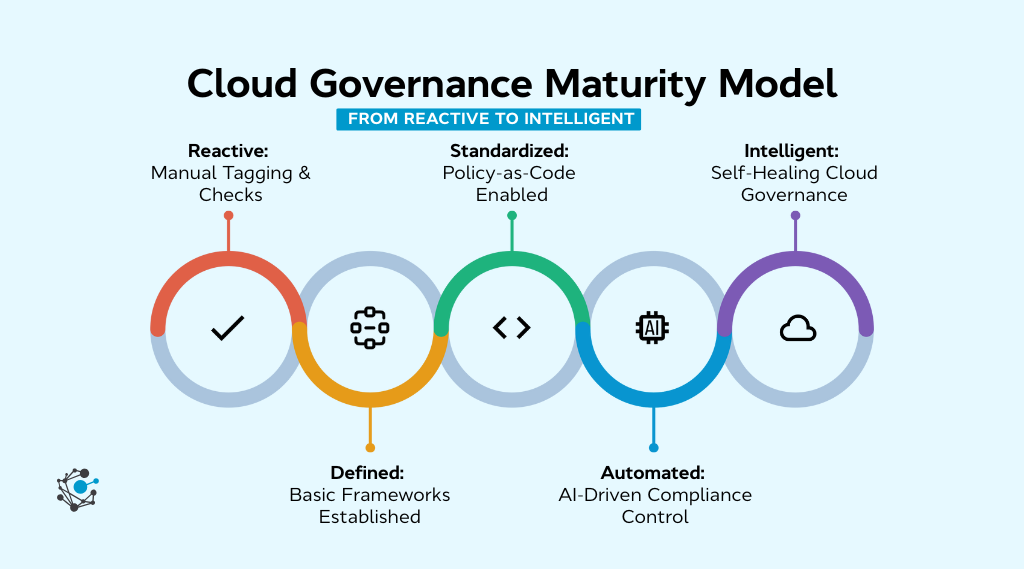
Why “2023 Model” No Longer Works
Governance frameworks of past depended on manual review as well as static Excel spreadsheets for tracking costs and patching security reactively. As of 2026 these frameworks are no longer relevant because of three main disruptive factors:
- Artificial Intelligence Sprawl (Shadow AI): Teams are creating expensive GPU clusters and accessing private data through LLMs and LLMs resulting in massive costs as well as security risk.
- Sovereignty & Compliance: Regulations such as those of EU Data Act and DORA (Digital Operational Resilience Act) require strictest automated verification of residency in data and operational resilience.
- The speed of remediation: Human operators cannot respond quickly enough “drift.” If resource is not compliant problem must be automatically remedied through software not as an item in queue.
This guide gives model to create development of cloud governance framework 3.0 one that is automated as well as AI driven and aligned with business needs.
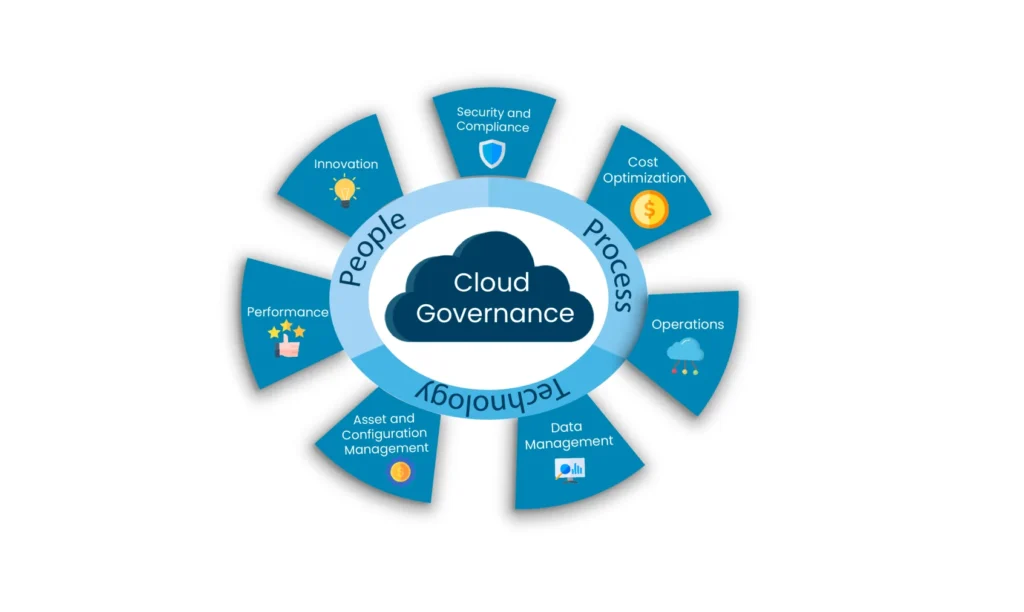
Core Pillars of 2026 Governance Framework
Modern frameworks are built on four different four pillars. Contrary to earlier models which separated “Security” and “Operations” model of 2026 combines both under umbrella of Policy as Code.
Pillar 1: Financial Governance (FinOps & GreenOps)
- The goal is to Maximize value for business and not just cut costs.
- Key Shift: Moving from “Showback” (reporting costs) to “Unit Economics” (measuring cost per transaction/customer).
- 2026 Context This includes GreenOps tracking carbon intensities of work. Policies of governance now require that batch jobs be run in regions that have lowest carbon footprint and during non peak energy usage hours.
Pillar 2: Security & Identity Governance (Zero Trust)
- Goal: Identity is new line of sight.
- Key Shift Transitioning away from static IAM roles to Just in Time (JIT) access and Non Human Identity (NHI) management.
- 2026. Context: Governance must specifically concentrate on “Agentic AI” software agents acting for humans. policies must limit what agents are able to do and ensure that they do not hallucinate possibility of escalating permissions.
Pillar 3: Operational Governance (Reliability & Performance)
- The goal is ability to be consistent and resilient.
- Key Shift Moving from “ClickOps” (manual console changes) to strictly controlled infrastructure as code (IaC).
- 2026 context: Platform Engineering takes center of stage. Governance is built into “Golden Paths” or Internal Developer Platforms (IDPs). When developer is using platform theyre already compliant.
Pillar 4: Data & AI Governance (Sovereignty & Ethics)
- The goal: Data residency security and AI that is responsible.
- Key Shift From safeguarding “storage buckets” to protecting “inference endpoints.”
- 2026 Context ensuring that data from proprietary sources doesnt get absorbed into training models that are publically available. Insisting on “Data Sovereignty” where German data is kept at Frankfurt while Indian data remains in Mumbai and Mumbai without exemptions.
3. Governance Model: People Process and Technology
Frameworks are nothing without structure supporting it. By 2026 organization structure has been flattened to facilitate agility.
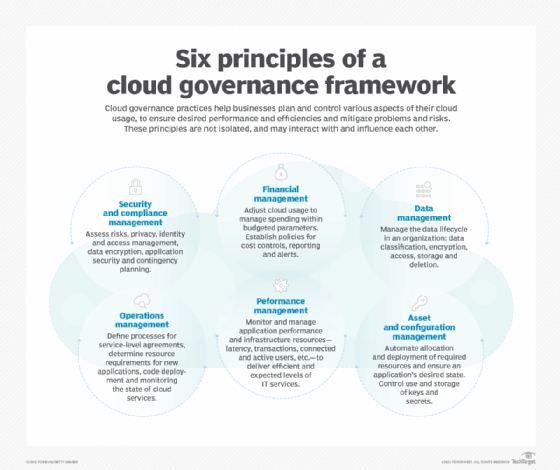
A. People Cloud Center of Excellence (CCoE) against. Platform Team
The conventional CCoE was often an obstruction. Modern CCoE splits responsibility:
| Role | Responsibility | 2026 Evolution |
| Cloud Steering Committee | Strategy & Budget | Particularly focused on AI ROI as well as multi cloud vendor strategies. |
| Platform Engineering Team | Builds Guardrails | creates”the “vending machine” for compliant cloud accounts. |
| Embedded Guardians | Enforces Local Standards | DevOps heads within departments of product that are responsible for particular oversight of their application. |
| FinOps Practitioner | Cost Optimization | It is now specialized job usually reporting to CFO but not CTO. |
B. Process: Governance Lifecycle
Governance isnt once only setting. Its loop
- Definition: Write policy (e.g. “All storage must be encrypted”).
- Codify Transform policy to codes (e.g. OPA Rego Terraform Sentinel).
- Avoid: Block non compliant builds within pipeline of CI/CD.
- Detected: Scan running environments to detect drift.
- Resolution: Automatically fix shift (e.g. remove bucket that is not encrypted).
- Measuring: Dashboard compliance score.
C. Technology: Governance Mesh
No longer do we depend on one tool. tools we use are collection of interconnected tools
- Policy Engines: Open Policy Agent (OPA) Kyverno.
- CSPM (Cloud Security Posture Management): Wiz Orca Prisma Cloud.
- FinOps Platforms: Apptio Vantage Kubecost.
- IDP (Internal Developer Portal): Backstage Port.
4. Detailed Implementation Guide: Building Framework
This chapter outlines step by step implementation of framework.
Phase 1: Foundation & Visibility (The “Read Only” Phase)
Before you can be leader it you have to see.
1.1 Global Tagging Strategy
In 2026 tag is basis of governance. In absence of tags automated systems will fail. It is essential to enforce “Tag or Block” policy at stage of deployment.
- Mandatory Tags:
- CostCenter to chargeback.
- Owner Email address of person responsible for team or human.
- Environment: Prod Dev Sandbox.
- DataClassification: Public Confidential Restricted.
- Timeline: (New for 2026) When resource will be instantly re evaluated or deleted.
1.2 Hierarchy & Account Structure
Dont use flat structure of your account. Utilize deep nesting hierarchy to transfer rules.
- AWS: AWS Organizations > OUs (Security Sandbox Workloads > Prod/Non Prod).
- Azure: Management Groups > Root > Landing Zones > Subscriptions.
- GCP: Organization > Folders > Projects.
Best practice: Apply “Deny” rules at root Level (e.g. deny deployments in regions that are not approved). Implement “Audit” policies at leaf level in order to provide flexibility to be flexible while ensuring visibility.
Phase 2: Guardrails & Prevention (The “Gatekeeper” Phase)
This step is one that moves to governance “Left” into code pipeline.
2.1 Policy as Code (PaC)
Stop writing PDF policies. Create codes.
- scenario: You want to block from being able to access public S3 buckets.
- Old Fashioned: Security analyst checks daily on console.
- 2026 Way (Terraform/Sentinel):
Terraform
rule “enforce s3 private”
If an author attempts to publish code via an open bucket and pipeline is unable to complete it right away.
2.2 “Golden Image” & Artifact Repository
Developers shouldnt download binaries via internets open source. Governance demands controlled “Artifactory” or “Container Registry.”
- The only approved scans approved and hardened images are allowed to be utilized.
- Governance is system that automates this “re hydration” of these images daily using most recent patches for security.
Phase 3: Automation & Remediation (The “Autopilot” Phase)
It is ineffective if there is no any action.
3.1 Event Driven Remediation
Make use of Event bridges (e.g. AWS EventBridge Azure Event Grid) to invoke serverless operations (Lambda/Functions) whenever policy is violated.
- Drift Exemple: user manually connects to Port 22 (SSH) on firewall of production.
- Automated Response:
- EventBridge detects AuthorizeSecurityGroupIngress.
- Lambda function activates.
- Lambda takes away rules immediately.
- Lambda post message on particular Slack channel that user is on: “Port 22 access was revoked. Please use JIT access portal. “
3.2 Automated Budget Enforcement
FinOps by 2026 could be very aggressive.
- Soft Limits: At 80% budget contact your team.
- The Hard Limit is: At 110% budget it will stop creation of new sources from being developed.
- Nuclear Limits: (For Sandbox accounts only) at 120% budget at which point you can start an “Nuke” script that terminates use of all computing resources in order in order to stop bleeding.
Phase 4: AI Governance (The “New Frontier”)
It is only new feature for landscape of 2026.
4.1 Governing AI Models
- Model Registry Every AI models have to be registered in an online catalog (like MLflow) with lineage tracking. It is essential to know information was used to train model.
- Rate Limiting In order to avoid “Wallet Denial of Service” (running through enormous API charges) governance should set strict rate limits for Inference Endpoints on API Gateway at API Gateway level.
4.2 Data Sovereignty for AI
- Guidelines: “No PII (Personally Identifiable Information) can be sent to public LLM endpoints.”
- Methodology: Install use of an “AI Gateway” or proxy which connects your applications to external models (e.g. OpenAI/Anthropic). gateway makes use of DLP (Data Loss Prevention) to search for credit cards and SSNs and remove data prior to request is removed from your system.
Tools & Technologies Landscape (2026)
The toolchain has been consolidated. Businesses now choose platform solutions over point solutions.
| Category | Native (Cloud Provider) | Third Party (Enterprise) | Open Source / Cloud Native |
| Policy Engine | AWS Config Azure Policy | HashiCorp Sentinel Styra | Open Policy Agent (OPA) Kyverno |
| Cost / FinOps | AWS Cost Explorer Azure Cost Mgmt | CloudZero ProsperOps (Auto savings) | OpenCost |
| Security / CSPM | AWS Security Hub Defender for Cloud | Wiz Palo Alto Prisma | CloudSploit Prowler |
| Identity / CIEM | IAM Access Analyzer | CyberArk Okta | Teleport (Access Plane) |
| Platform / IDP | AWS Proton | Mia Platform Harness | Backstage |
Selection Advice:
- For Multi Cloud avoid native tools. Utilize Terraform or Wiz with OPA for one “pane of glass” for rules for AWS Azure and GCP.
- If you want to use single cloud take deeper dive with native tools (e.g. Azure Policy is extremely effective if youre completely Azure).
Common Challenges & Best Practices
In 2026 even humans are cause of friction.
Challenge 1: “Governance Slows Us Down”
- The Friction developers bypass controls since process of approval is very slow.
- The solution for 2026: Shift Left and self service. Do not make customers wait around for ticket. They will be given pre approved “Landing Zone” code module. If they decide to utilize program they do not need any review boards.
- Mantra “The path of least resistance must be compliant path.”
Challenge 2: Managing Multi Cloud Consistency
- The Frustration: Mapping “S3 Bucket Encryption” (AWS) to “Blob Storage Encryption” (Azure) is time consuming.
- The 2026 Solution: Use Unified Policy Layer. Software such as OPA permit you to record intention (“Storage should be secured”) and assign intent to specific types of resources across different clouds.
Challenge 3: Shadow AI
- The Friction Employers who use their personal ChatGPT accounts to obtain company codes.
- The solution for 2026: You cannot block AI. It is necessary to provide corporate AI. Create private secure corporate example of an LLM. If you offer them right device they wont choose one that isnt safe.
Future Trends: Looking Beyond 2026
How will governance evolve in future?
Autonomous Governance (AI Governing AI)
There will be rising in number of “Governance Agents.” They are AI models that have been trained on particular compliance documents that you provide as well as architecture designs.
- The Agent asks developer: “I need pattern for HIPAA compliant healthcare app. “
- The Agent produces Terraform code pre configured with necessary encryption logs and backup policies and installs it.
Continuous Compliance Auditing
“Annual Audit” is dead “Annual Audit” will die. Auditors will use your governance API in real time to get “Compliance Credit Score” that is updated each minute.
Conclusion: Your Immediate Next Steps
The creation of an Cloud Governance Framework in 2026 is test of balance between control and latest technological advances. aim is to create safeguards that appear unnoticed by user however are not able to be broken by danger.
Checklist to Start Today:
- Check your Tagging If youre able to achieve 90 percent coverage of your tags you need to put it down and make changes.
- Take Budget Actions Set up automated alerts for any cost anomalies right now.
- Scan for public Resources: Run Prowler scan or Wiz scan to discover every public IP and bucket.
- Set out AI policy: Publish clear document that outlines how to use AI use by employees.
- Options Trading Automation Using Python: Complete Beginner Guide
- Synthetic Data Generation: The Ultimate Master Guide 2026
- GitHub Copilot Master Guide 2026: The Ultimate AI Coding Handbook
- How Accurate Are AI Content Detectors Master Guide 2026
- Cloud Native Database Architecture Step by Step for Beginners Master Guide 2026